Michele Toccagni
Cyber Security Operation Lead @ ING BankA Penetration Tester with 5+ years of experience in penetration testing on various applications in different domains. Ability to read and analyze code, from Java to .NET. Have hands-on experience in security research along with different security testing tools.
Work Experiences
Cyber Security Operation Lead
ING Bank
- Leading a proficient team in executing offensive security evaluations (SAST, Penetration test, Vulnerability Assessment, etc.) and implementing robust defensive measures (Threat Intelligence, Data Loss Prevention, etc.) to fortify organizational resilience against cyber threats.
- Managing relationships with service vendors and ensuring seamless collaboration for maximum efficiency.
Security Associate Manager - Penetration Tester
Accenture Italy
- Involved in the security analysis of infrastructures, with focus on Web, Network, Mobile and Thick Client Penetration Test.
- Developed a tool to generate automatically the reports of Penetration Tests (like Serpico). This tool is written in Python-Flask, create both Word and Excel reports and it's used by the whole team.
- Team management, both in managing activities and in relations with clients.
- Coordinate and direct all phases of product testing while managing and leading project teams.
- OSINT and Threat Intelligence activities.
Security Audit
Argo Software
Collaboration with Alpha Institute of Geopolitics and Intelligence
Malware Analisys for the Ransomware Report 2016
Penetration Test Skills
WEB
- Deep knowledge of OWASP Top 10.
- Knowledge of Advanced Attacks, like Bypass CSRF, Blind XXE and so on.
- Daily usage of tools like Burp Suite, OWASP ZAP, SQLmap, nikto, etc.
- Ability to perform a deep analysis on decompiled web app source code.
- Ability to exploit vulnerabilities by chaining them into complex attacks.
Mobile
- Deep knowledge of OWASP Top 10 Mobile.
- Static and Dynamic Analysis on Android and iOS applications.
- Usage of tools like Jadx, Objection, Frida, etc.
- Ability to read Java in order to craft custom exploit.
Network
- Using information gathering techniques to identify and enumerate targets running various operating systems and services.
- Conducting remote, local privilege escalation, and client-side attacks.
- Leveraging tunneling techniques to pivot between networks.
- Knowledge of bash scripting and python in order to create custom exploit.
Thick Client
- Ability to enumerate services on Windows Platform.
- Knowledge of Decompilation tool like Dnspy, DotPeek, etc.
- Ability to perform a deep analysis on decompiled windows app source code.
- Ability to exploit vulnerabilities by chaining them into complex attacks.
- Proficiency in scripting, Unix operating systems and windows
Soft Skills
- Ability to communicate technical vulnerabilities to developers and C-Level.
- Managed the activities from the planning to the delivery.
- Worked with application developers to validate, assess, understand root cause and mitigate vulnerabilities.
Education
Laurea Magistrale (Master), Cyber Security
University of Milan
Milan, Italy
Laurea Triennale (Bachelor), Comunicazione Digitale
University of Milan
Milan, Italy
Liceo Scientifico Tecnologico
I.S.I.S G. Natta
Bergamo, Italy
Mentions
Blog post for Alpha Institute
Prevenzione e contromisure per CTB-Locker
Primo passo della caccia al bug con hacking etico
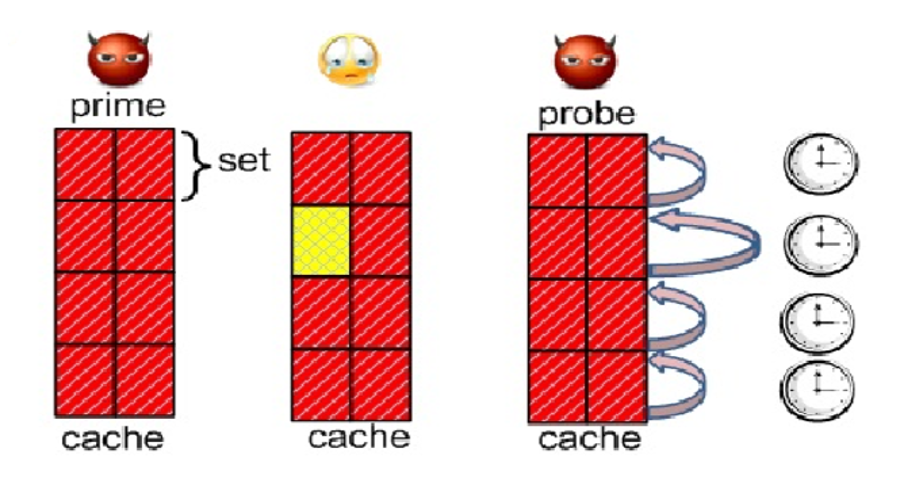
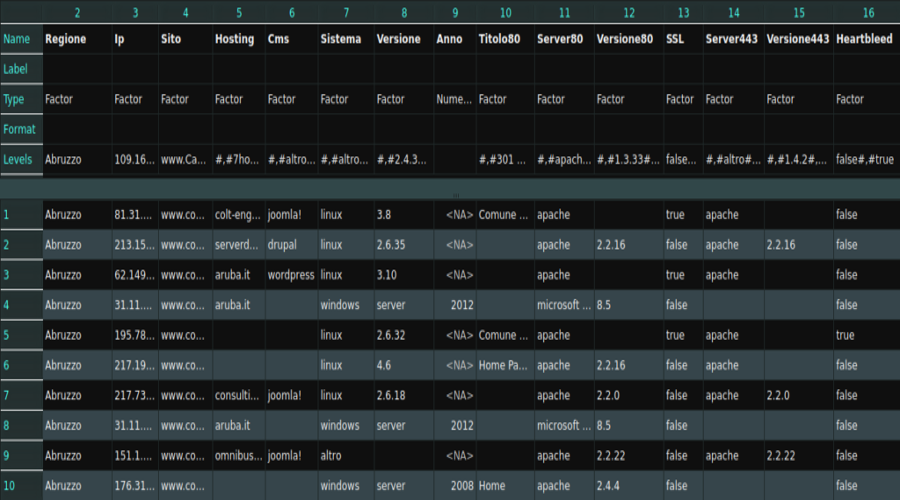
A blog post about the research that I've done on the websites of the cities of Italy
Awards
OSCP Certified
Obtained in June 2019
Telecom Italia - Hall of Fame
I've found an SQL Injection on a site managed by Telecom Italia
GIAC Mobile Device Security Analyst (GMOB)
Obtained in August 2021
Fastweb - Hall of Fame
I've found vulnerabilities on some sites managed by Fastweb
CVE-2020-13872
I identified a vulnerability in the Royal TS software that allows to bypass authentication
CERT-EU - Hall of Fame
I've found a vulnerability on a site managed by Europe.eu
OSED Certified
Obtained in June 2023
Contact
contact [at] toccagni {dot} info